The Ultimate Guide To Netmask 26: Understanding Subnetting In Networking
Netmask 26 is a crucial concept in the realm of computer networking, particularly when it comes to subnetting. As the need for efficient IP address management grows, understanding netmasks becomes increasingly important for IT professionals and network administrators. In this comprehensive guide, we will delve into the intricacies of netmask 26, its significance, and how it impacts network design and security.
In the following sections, we will explore the definition and function of netmask 26, how it compares to other netmasks, and its practical applications. We will also provide examples and tips for effective subnetting, ensuring that you have a solid grasp of this important networking concept.
Table of Contents
- What is Netmask 26?
- Binary Representation of Netmask 26
- Subnetting Explained
- Number of Hosts in a Netmask 26
- Comparing Netmask 26 with Other Netmasks
- Practical Applications of Netmask 26
- Challenges and Solutions in Subnetting
- Best Practices for Using Netmask 26
What is Netmask 26?
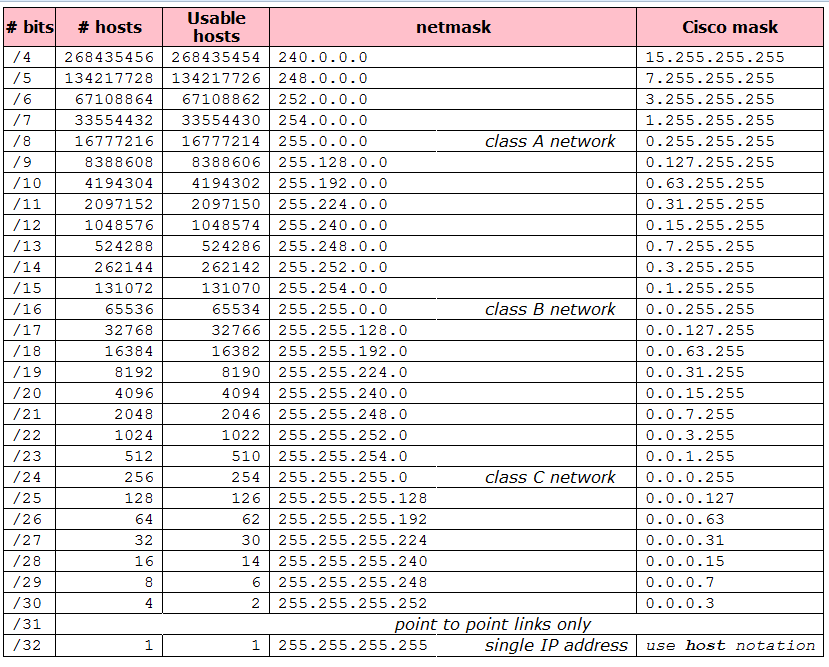
Netmask 26, often represented as /26, is a subnet mask that allows for efficient IP address management within a network. In a /26 subnet, the first 26 bits of the address are used to identify the network, while the remaining 6 bits are reserved for host addresses. This configuration allows for a total of 64 IP addresses in the subnet, with 62 usable for devices, as two addresses are reserved for the network and broadcast addresses.
Binary Representation of Netmask 26
The binary representation of netmask 26 is 11111111.11111111.11111111.11000000. To better understand this, let's break it down:
- The first three octets (11111111.11111111.11111111) represent the network part.
- The last octet (11000000) indicates that 26 bits are used for the network and 6 bits for hosts.
Subnetting Explained
Subnetting is the practice of dividing a larger network into smaller, more manageable sub-networks. This is essential for improving network performance and security. By using a netmask like 26, network administrators can create distinct subnets that can isolate segments of the network, reducing broadcast traffic and enhancing security measures.
Benefits of Subnetting
- Improved network performance due to reduced broadcast domains.
- Enhanced security through network segmentation.
- Efficient IP address management.
- Better control over network traffic.
Number of Hosts in a Netmask 26
As mentioned earlier, a netmask of 26 allows for a total of 64 IP addresses. However, since two addresses are reserved (one for the network and one for the broadcast), the number of usable host addresses is 62. This means that you can comfortably connect 62 devices within a /26 subnet.
Comparing Netmask 26 with Other Netmasks
To fully appreciate the significance of netmask 26, it’s helpful to compare it with other common netmasks:
| Netmask | Subnet Size | Usable Hosts |
|---|---|---|
| /24 | 256 IP addresses | 254 usable hosts |
| /25 | 128 IP addresses | 126 usable hosts |
| /26 | 64 IP addresses | 62 usable hosts |
| /27 | 32 IP addresses | 30 usable hosts |
As the table illustrates, as the subnet mask increases (i.e., more bits are allocated for the network), the number of usable host addresses decreases. This understanding is crucial for network design and planning.
Practical Applications of Netmask 26
Netmask 26 is commonly used in various networking scenarios, such as:
- Small to medium-sized networks where 62 devices need to be connected.
- Creating isolated subnets for different departments within an organization.
- Designing virtual local area networks (VLANs) in enterprise settings.
- Efficiently managing IP address allocation in cloud environments.
Challenges and Solutions in Subnetting
While subnetting is a powerful tool, it can also present challenges, such as:
- Complexity in managing multiple subnets.
- Potential for misconfiguration leading to connectivity issues.
- Difficulty in scaling networks as the organization grows.
To overcome these challenges, network administrators can implement the following solutions:
- Utilizing network management tools to monitor and manage subnets.
- Establishing clear documentation for subnet configurations.
- Regularly reviewing and updating subnet designs based on current needs.
Best Practices for Using Netmask 26
To make the most of netmask 26, consider the following best practices:
- Plan your subnetting strategy before implementation to avoid future complications.
- Document your IP address allocation and subnet configurations thoroughly.
- Regularly audit your network to ensure optimal performance and security.
- Stay updated on networking trends and best practices to continuously improve your skills.
Conclusion
In summary, netmask 26 is an essential aspect of subnetting that enables efficient IP address management and network organization. By understanding its structure, function, and practical applications, network professionals can enhance their network designs and improve overall performance. We encourage readers to explore further by leaving comments, sharing this article, or checking out other related articles on our site.
Final Thoughts
Thank you for taking the time to read this comprehensive guide on netmask 26. We hope you found it informative and beneficial for your networking endeavors. Be sure to visit us again for more insights and tips on networking and technology!